Version 6.2 for Secure Remote Worker and ThinKiosk has just been released, and with this new version comes a host of enhancements to the existing framework which can be seen here. However, in this blog I wanted to run through the major additions that have been made to Secure Remote Worker and ThinKiosk.
Profile Encryption
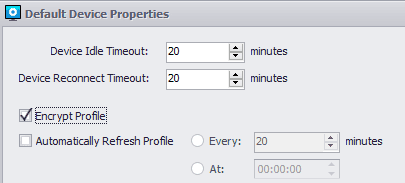
First and foremost, one of the changes that 6.2 brings to Secure Remote Worker specifically is that the solution will now ONLY accept encrypted profiles. This is to ensure the security of all information within the Secure Remote Worker profile. Due to this change, please ensure that your profiles have been encrypted via the ThinScale Management Platform:
More detail on this can be found in our ThinScale Knowldege Base
Multi-Volume Write Filter
If you missed our write filter implementation back with Secure Remote Worker 6.0, it essentially intercepts any writes to the drive within Secure Remote Worker and redirects them to a virtual overlay within a temporary location, which is then destroyed upon exiting Secure Remote Worker. This is in place to prevent any data leakage from the secure session to the personal machine.
Now the Write Filter is applied across all NTFS volumes, preventing data from being saved anywhere on the machine while the Secure Remote Worker session is active.
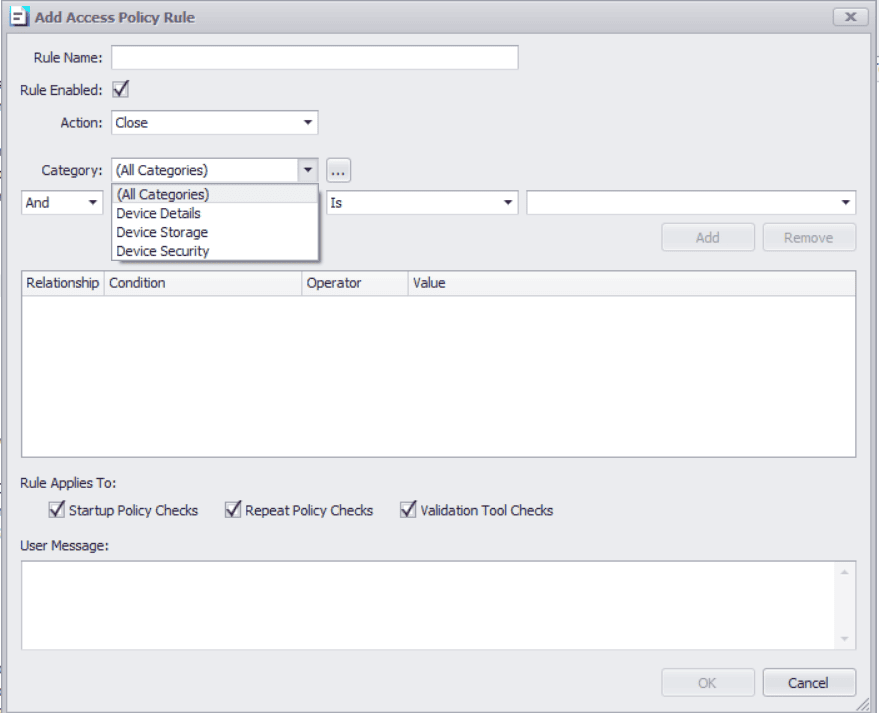
Access Policy
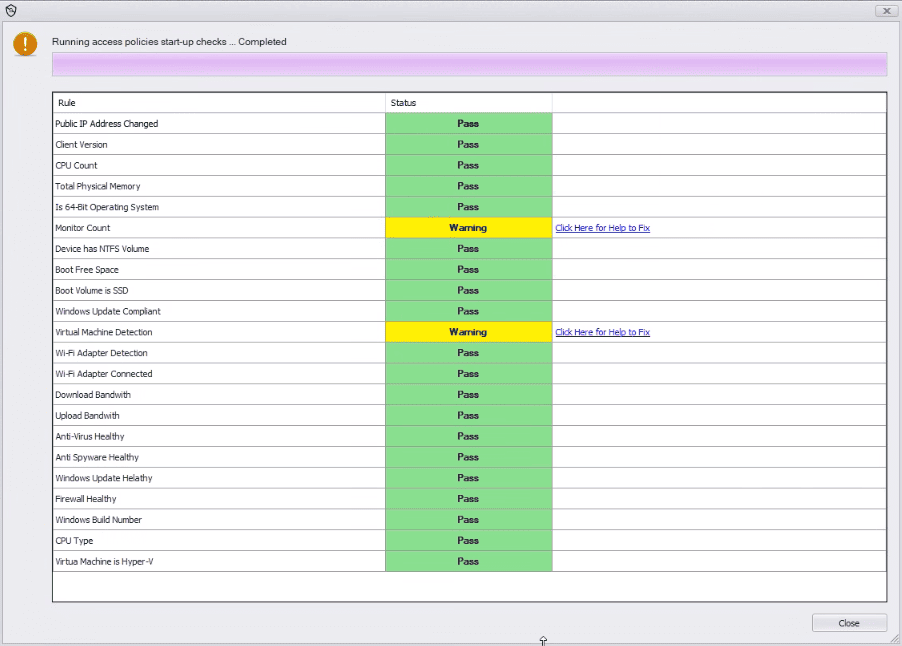
With this new feature, Secure Remote Worker and ThinKiosk machines can now run pre-configured checks on computer hardware and network status.
These checks can include Hard disk space, RAM, processor speed, network bandwidth, connected hardware, & much more.
The IT team can dictate what checks will be performed on employee machines, and even how frequently these checks are performed.
Access Policy can be configured to run at device startup to ensure devices continue to meet company standards.
Access Policy can also run alongside Secure Remote Worker’s Validation Tool to provide additional hardware checks on top of the existing vetting of things such as: anti-virus, firewall, Windows update status, etc. pre-installation.
Recently, we have seen companies incorporating device readiness into their recruitment strategy for WaH employees, with the Validation Tool acting as they key piece in this early verification process. The new Access Policy feature pushes this even further and lets employers drill down into the machine’s hardware and set standards for device specifications, this will help assure that new hires have compatible devices from the get go. Meaning faster onboarding, a better experience for the employee, and increased productivity.
Companies utilizing the Validation Tool as part of their onboarding process can now use Access Policy to greatly enhance their device vetting process.
Whether ensuring corporate devices maintain a certain level of performance, or including hardware checks in personal device readiness testing, Access Policy allows IT an even greater level of control over devices accessing their ThinKiosk and Secure Remote Worker environments.
Read all about the new 6.2 update in the ThinScale Knowledge Base.